Here we offer guidelines for configuring the MS Exchange APIs and creating the application on the Azure Active Directory. The configuration process is divided into the following sections:
-
Creation of new account on Azure portal along with steps to register a new application.
-
Adding permissions to the registered application.
-
Configuration on backend application along with Postman & Swagger document for using APIs.
It is important to acknowledge that certain configurations within the Azure Portal have the potential to create issues or impede specific functionalities of this service. It is important to highlight that this document is unable to furnish configuration steps or information for exceptional scenarios of this nature.
Prerequisites / Limitations
imc Learning Suite
-
The feature is tied to a licensed add-on in imc Learning Suite “Resource Management Licence”
-
The backend and frontend URL need to be configured in the configuration properties
-
Set up available only for resource type “Room”
-
The resource “Room” needs to be manually configured in imc Learning Suite with an external ID, which identifies the meeting room across all other rooms in MS Exchange
-
Only the booking process is supported, prebooking/preplanning is not available for external resources
-
It is not possible to do multiple bookings of the same room in the same time interval.
-
Downtime and checklist functionalities are not possible for external resources.
-
For course templates the external resources are not available to be added
-
In the resource calendar the availability of external resources can be checked for a maximum of 1 month.
Benefits
Azure/MS Exchange
-
The service ”External Resource Connector” needs to be configured to be part of the delivery package
-
A Teams tenant is needed (usually included in an Office 365 subscription / tenant)
-
A technical user / app needs to be created to access the Microsoft Graph API with specific permissions
-
Automated import to imc Learning Suite for available rooms from the active directory is not supported, this needs to be done manually
-
External resources are available only for date dependent courses, since this is a limitation from MS Exchange when requesting the availability of resources
-
The maximum time interval for checking a room is 1 month, it is a limitation from MS Exchange.
Functions Overview
-
Rooms as resources can be selected in resources management in imc Learning Suite from MS Exchange.
-
Availability status of rooms are provided by the provider and transferred vice versa.
-
Create multiple external providers of the type Resource Account and ensure in a multi-tenant system, where users belong to different tenants that they can use different Exchange installations.
Pre-Configuration
Creation of the Technical User / App
System Requirements
Application / Web Server
|
Product |
Version |
|---|---|
|
Tomcat |
9 |
Technology Stack
The following table provides a list of the technologies used to implement MS Exchange.
|
Name |
Version |
|---|---|
|
Java |
17.0 |
|
Spring Boot |
2.7.11 |
|
Gradle |
7.6.1 |
|
Microsoft Graph SDK |
5.30 |
|
Junit |
4.12 |
|
Lombok |
1.18.10 |
|
Azure Identity |
1.2.5 |
Integration Steps
Register New Application on Azure Portal.
To register a new application using the Azure Portal follow these steps:
-
Sign in to the Azure portal using either a work or school account or a personal Microsoft account.
-
If the account gives access to more than one tenant, select the account in the top right corner, and set the portal session to the Azure AD tenant that is wanted.
-
In the left-hand navigation pane, select the Azure Active Directory service, and then select App registrations > New registration.
-
When the Register an application page appears, enter the application's registration information:
-
Name - Enter a meaningful application name that will be displayed to users of the app.
-
Supported account types - Select which accounts the application should support.
-
|
Supported Account types |
Description |
|---|---|
|
Accounts in this organisational directory only |
Select this option when building a line-of-business (LOB) application. This option is not available if the application is not being registered in a directory. This option maps to Azure AD only single tenant. This is the default option unless registering the app outside of a directory. In cases where the app is registered outside of a directory, the default is Azure AD multi-tenant and personal Microsoft accounts. |
|
Accounts in any organisational directory |
Select this option if targeting all business and educational customers is wanted. This option maps to an Azure AD only multi-tenant. If the app is registered as Azure AD only single-tenant, the app can be updated to be Azure AD multi-tenant and back to single-tenant through the Authentication blade. |
|
Accounts in any organisational directory and personal Microsoft accounts |
Select this option to target the widest set of customers. This option maps to Azure AD multi-tenant and personal Microsoft accounts. If the app is registered as Azure AD multi-tenant and personal Microsoft accounts, it cannot be changed this in the UI. Instead, the application manifest editor must be used to change the supported account types. |

Redirect URI (optional) - Select the type of app being built, Web or Public client (mobile & desktop), and then enter the redirect URI (or reply to URL) for the application. This option is optional and can be skipped.
When finished, select Register.
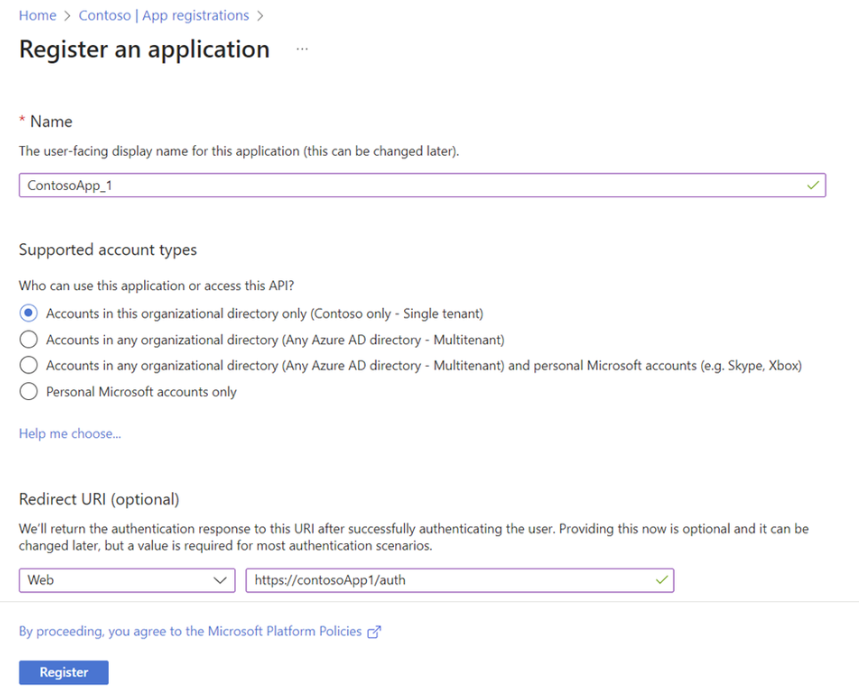
Azure AD assigns a unique application (client) ID to the app, and the user is taken to the application's Overview page. To add additional capabilities to the application, select other configuration options including branding, certificates and secrets, API permissions, and more.
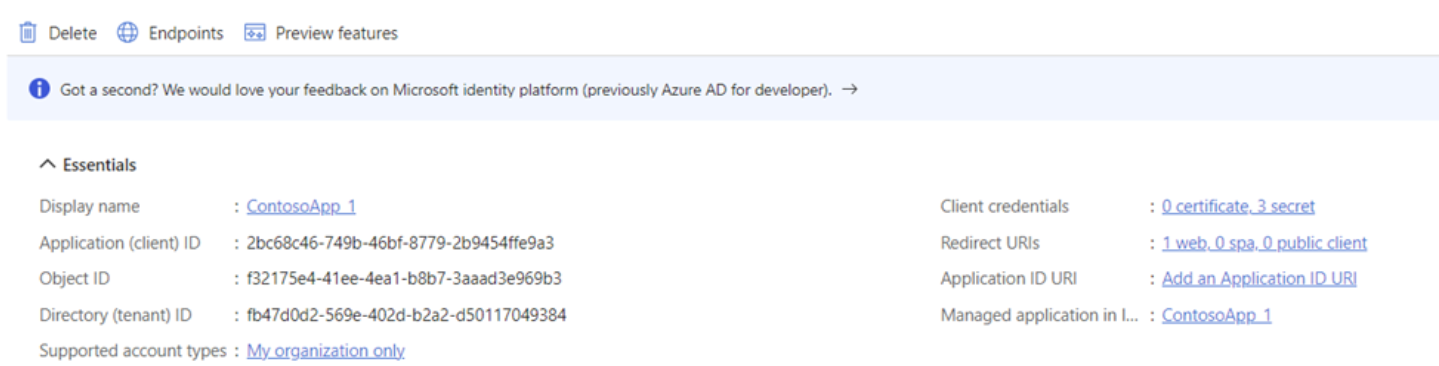
Adding Permissions to Registered Application
Permissions are essential for enabling specific functionalities within the registered application. These permissions grant the necessary access rights to perform various actions, for the registered application to create, fetch, update and delete calendar events.
To add permissions, perform below steps:
-
In the left-hand navigation pane, select the Azure Active Directory service, and then select App registrations. This will list all the registered applications. Now select the newly registered application. This will redirect to the overview page of application.
-
In left-hand navigation pane select API Permissions.
-
Click on Add a permission button and assign below permissions to the app at Application level and Grant admin consent:
|
Functionality |
Privileges |
Description |
|
Calendars.ReadWrite |
Creates an event to mark the resource as booked |
|
|
Calendars.Read (†) |
Returns a list of an user events. |
|
|
Calendars.ReadWrite |
Unbooks an event from the user's calendar |
|
|
Calendars.ReadWrite |
Updates an existing event from the user's calendar |
Note: Permission not needed if Calendars.ReadWrite permission has already been granted, as Calendards.Read is contained within the Calendards.ReadWrite privilege.
This is a compilation of all APIs employed by the service from the Microsoft Graph, accompanied by the corresponding required privileges for invoking each API. In instances where specific functionalities are deemed unnecessary or certain privileges cannot be given, reference to this list is recommended.
We strongly recommend granting all required privileges to provide full functionalities provided by the service.
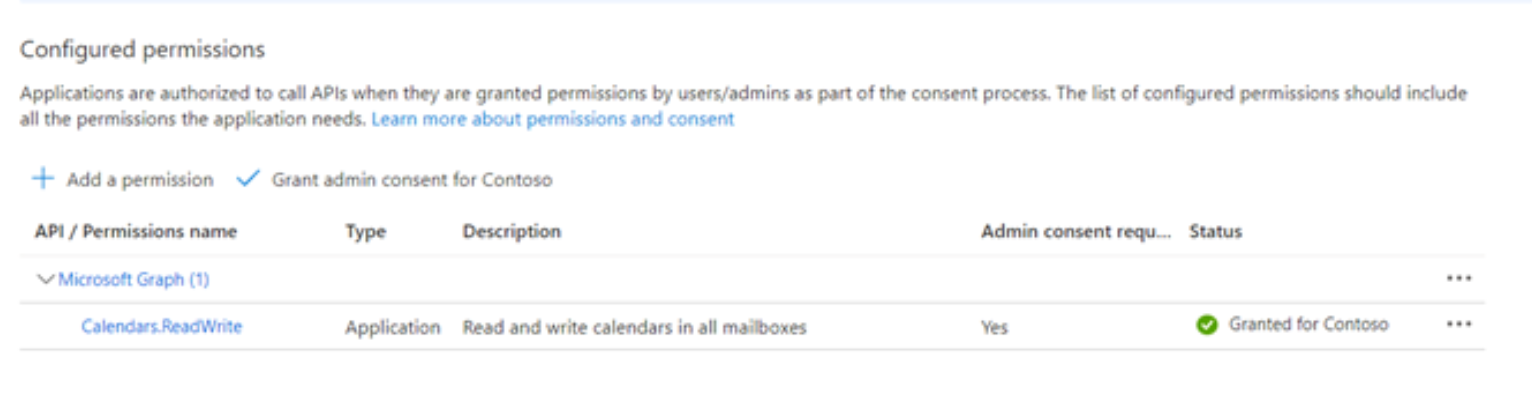
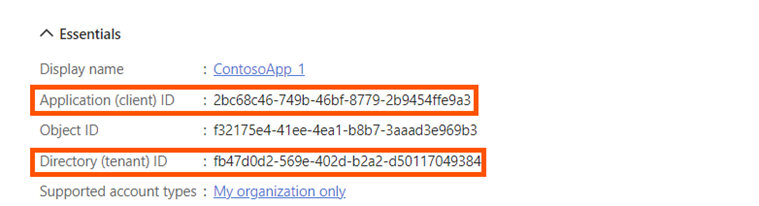
Application Credentials
Upon successful creation of a new application, it is automatically assigned a unique application (client) ID. This ID is crucial for identifying the specific application and tenant (organization) to which requests are to be sent.
There are 3 values that are used to authenticate each request from the service to the Microsoft, and those are:
-
Application (Client) ID
-
Tenant ID
-
Client Secret (value)
Client ID and Tenant ID values, can directly be seen from the applications overview page:
Initially, applications do not have a secret assigned to them, so there is the need to create one. To generate a new client secret, click on the Certificates & Secrets in the left menu of the applications setting

When adding a new secret value, it is essential to provide a concise description of its purpose and set an appropriate expiration date, as secrets cannot be permanent. We recommend setting the secret to a maximum validity period of 2 years.
The expiration date for the secret can be selected from the following options. However, it is important to consider that opting for a shorter validity period will necessitate more frequent updates within the External Service Provider page.
Configuration
Activate the Resource & Capacity licence
The service licence needs to be activated by the imc business consultant and can then be configured inside imc Learning Suite by the admin user. At the current state, the configuration is done in "User-defined parameters" and will be moved to an individual configuration section in the configuration manager.
External Service Provider
After the license is activated, create a new “Resource Account”. This is possible via the External service providers manager, by selecting Resource Account:
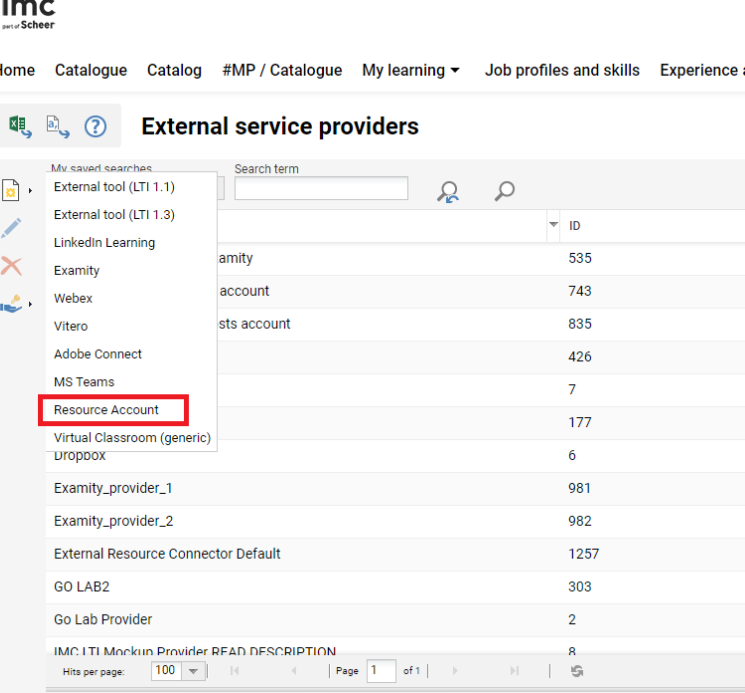
The system allows the admin to create multiple external providers of the type Resource Account. This ensures that in a multi-tenant system, users belonging to different tenants can use different MS Exchange installations.
The external service provider for MS Exchange requires a client ID, Client Secret and Tenant ID that must be obtained via the Azure Active Directory setup (please see Application credential).
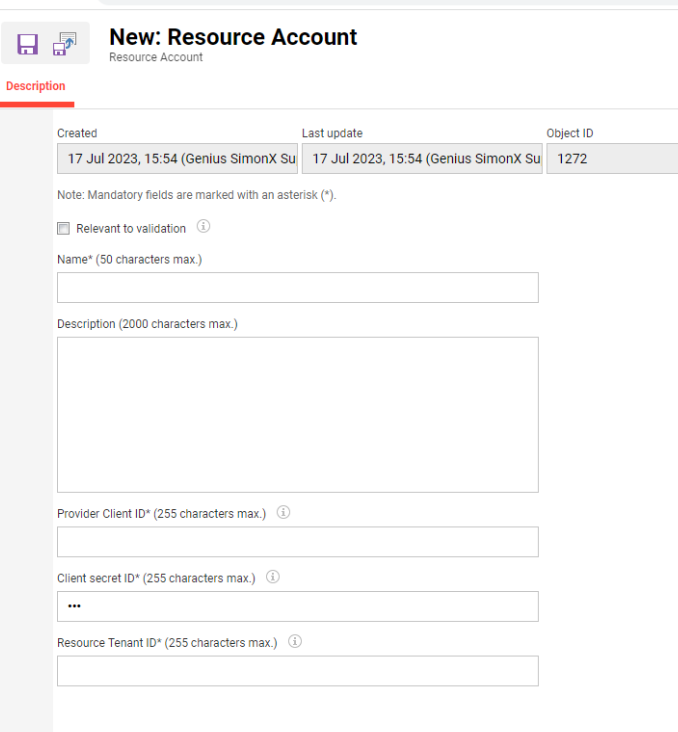
Resource configuration
After the license is activated, find the following configuration: Resource configuration in configuration manager.
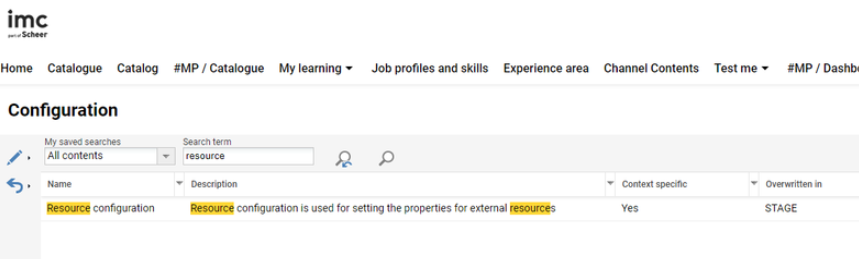
Edit this configuration if needed. Check the Enable external resource checkbox to enable the external resource configuration and add the URL of the external resource connector.

The detailed explanation of the parameters is given in below table:
|
Paramenter |
Description |
Example Value |
|
Enable external resources |
Used to generally enable or disable the integration |
true |
|
Resource service EndPoint |
API endpoint used for accessing resources; including external domain |
|
|
External service provider |
the external service provider used for authentication and connection to Microsoft Graph API |
here only the Resource Account external service can be seen |
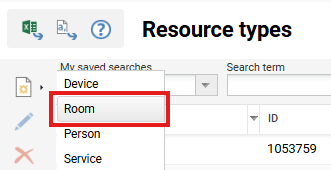
Create and configure an external resource type
After the service configuration is set up, we need to create an external resource which is linked to the resource provided by Exchange. For this purpose, the following are used:
-
Create a new Resource Type: Room
-
Go to the meta tag tab and add the meta tag: Resource is provided externally (10112)
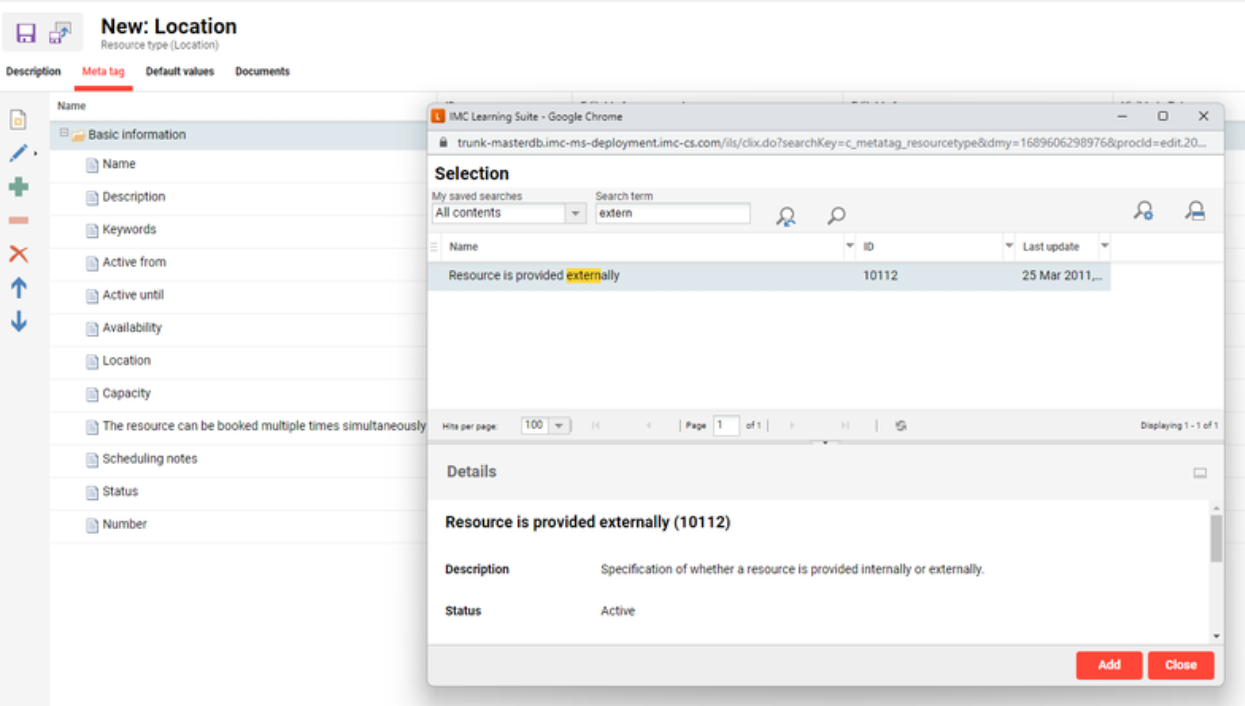
-
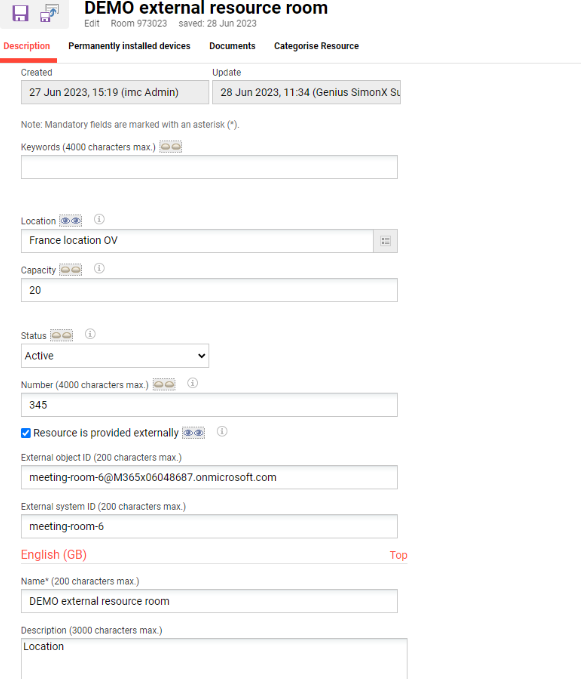
Switch to the default value tab. Because the external resource configuration is active, beside the meta tag there will be also 2 more fields available: External object ID and External system ID
|
Parameter |
Description |
Example Value |
|
Resource is provided externally (10112) |
Used to point that the resource is provided externally or not
|
checked:
unchecked:
|
|
External object ID |
this is the unique id of the resource used to be identified in MS Exchange, rooms are identified within an e-mail address. This field is mandatory if the metatag 10112 is checked. Field is unique for resources (only on media level) |
|
|
External system ID |
the external system id |
MS Exchange |
Important: A resource is considered to be externally provided if: Resource is provided externally (10112) is checked AND External object ID is not empty.
Create and configure an external resource
After creating the external resource type, create a new resource from that type.
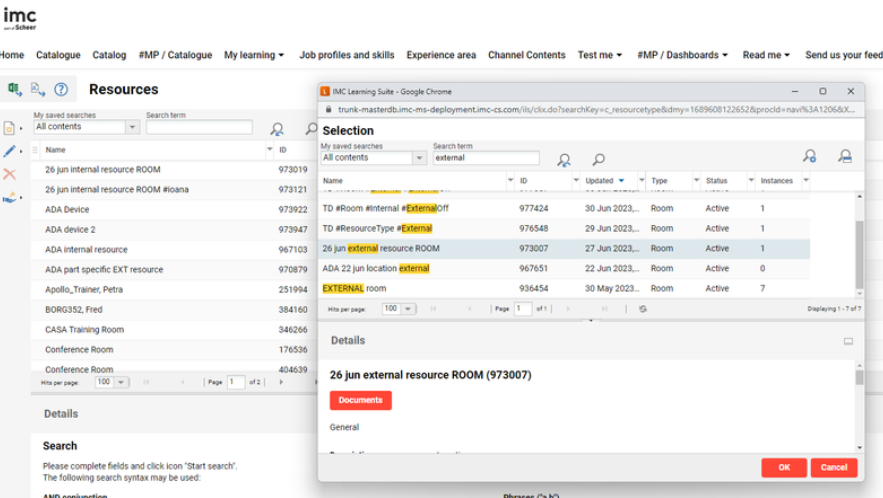
Use external resources inside imc Learning Suite
Inside courses / medias
-
Edit or create a course or media that has the Resource tab available
-
Navigate to resource tab
-
Click “Add button to select an external resource” which is only enabled if the configuration for using external resources is checked. At this point all external resources can be seen, that are configured as external in imc Learning Suite, ordered by availability. All data is retrieved from MS Exchange.

-
After this step the resource is displayed in the calendar.
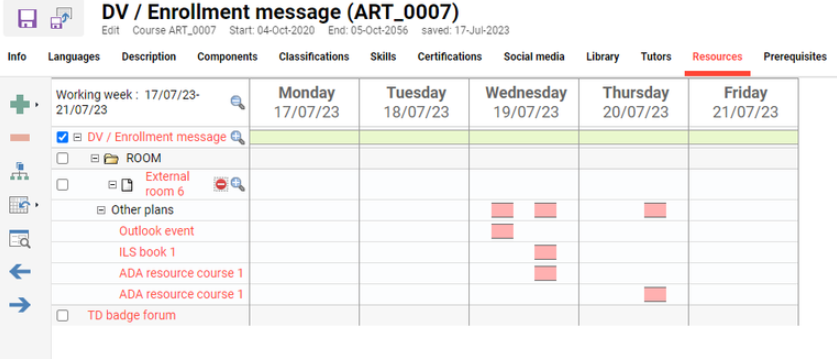
-
It is possible to book, create, edit, and send e-mail for external resources that are booked as stand-alone from imc Learning Suite, for the others, bookings that are related to components booking or bookings from outside imc Learning Suite, only to send e-mail is allowed.
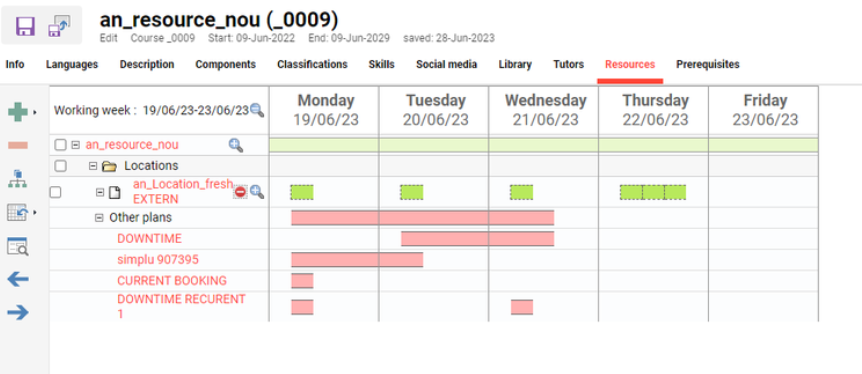
Resource Calendar
The View can be for a maximum of 1 month.
Book, create, edit, and send e-mail for external resources that are booked as stand-alone from imc Learning Suite, for the others, bookings that are related to components booking or bookings from outside imc Learning Suite, only to send e-mail is allowed.
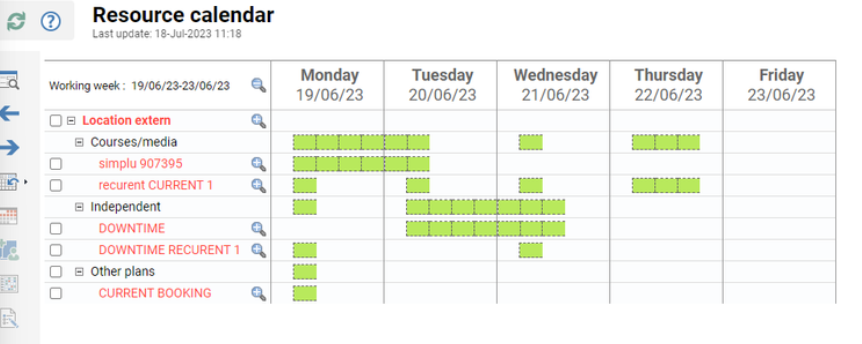
Tree view explanation:
-
Independent → all bookings from resource calendar done with the LMS
-
Course/media → component bookings for this resource
-
Other plans → all bookings which have no relation with the LMS
